We Value your Privacy
We value your privacy. No LLMs are trained on your data
SOC2 Type 2 Certified
We are SOC2 Type 2 certified. Your data is encrypted end-to-end
HIPAA Compliant
We safeguard Personal Health Information (PHI)
GDPR Compliant
We comply with GDPR regulations, ensuring your data privacy rights and control.
Enterprise Grade, Safe and Secure
Our commitment to data security:
We understand that when you use our platform, you trust us with your valuable data. That’s why we’ve implemented robust measures to ensure your information is always protected. Here are the features we’ve implemented to make this possible:Multi-Tenancy for Global Organizations
Storytell offers a robust multi-tenant structure, designed to simplify complexity while offering flexibility and control. Whether you’re a conglomerate with diverse regional branches or a multifaceted organization with varying departments, Storytell is engineered to cater to your needs with precision and ease.Tailored Multi-Tenant Solutions
The cornerstone of Storytell’s approach is our multi-tenant architecture that empowers worldwide organizations to operate numerous organizational units under a single umbrella, including scenarios like the following:Both a North American division and an APAC division can coexist independently yet communicate seamlessly within the same organizational structure. Each unit can have distinct settings and permissions tailored to its operational requirements without impacting others.
Streamlined Governance and Billing
Storytell’s clearly defined hierarchies ensure smooth governance and manage billing practices efficiently. Governance and billing protocols can be aligned across the organization, making it easier for businesses to standardize procedures and monitor compliance collectively. Users with top-level permissions gain comprehensive visibility across all assets and utilization metrics within the entire global tenant, enabling decision-makers to maintain a bird’s-eye view of the organization’s sub-tenants.End-to-End Encryption
All your data is encrypted end-to-end. This means that from the moment your data leaves your device until it reaches our servers, it is securely encrypted. No one can intercept or read your data during this transfer process.Data Encryption at Rest
In addition to end-to-end encryption, your data is also encrypted when it is stored on our servers. This ensures that even if someone were to gain unauthorized access to our storage, they would not be able to read your data.Provenance Chain
We maintain a detailed provenance chain for your data. This means we track where your data came from, who accessed it, and how it was used. This transparency allows you to see the entire history of your data, ensuring there are no blind spots in its custody. Here are the key details:- Origin Tracking: The provenance chain records where the data originated. This means that every piece of data within Storytell is tagged with its source, allowing users and administrators to trace it back to its initial entry point.
- Reference Tracking: The system also keeps track of who referenced the data. This includes identifying the specific individuals or entities that have interacted with or utilized the data within the platform.
- Contextual Usage: Storytell logs the specific thread or chat in which the data was referenced. This contextual information helps in understanding the circumstances and discussions surrounding the data’s usage.
- Distribution to LLMs: The provenance chain includes information about which large language models (LLMs) the data was distributed to. This ensures that any AI-driven processes or analyses involving the data are fully transparent and traceable.
- No Blind Spots: By maintaining this detailed chain of custody, Storytell ensures that there are no blind spots in the data’s history. Every interaction and movement of the data is accounted for, providing a robust audit trail.
No LLM Training with Your Data
All Storytell users (even on free usage plans) are protected. Storytell only uses enterprise APIs with LLMs. We do not allow your data to be used to train on any large language models (LLMs). Your data remains your own and is not used to improve AI models. This ensures that your information is not shared or used in ways you did not intend.Audit Logs
We have the capability to inspect and audit the provenance chain manually, providing an additional layer of security and accountability. These logs can show who accessed your data and when, providing an additional layer of security and accountability. We follow our SOC2 Type II protocols to determine who can access your data and under what circumstances.AI Firewall
Want to use Storytell not just at work, but also in life and play? You can. In fact, we encourage it. We’re building an AI firewall to segment your usage of Storytell at work vs. in life, with completely separate spaces for your work vs. personal data, ensuring that knowledge and data do not cross over between these spaces. This will be particularly useful for users who might use Storytell for both personal and professional purposes, our users often tell us they do. Request early access to this feature.Continuous Monitoring and Updates
We continuously monitor our systems for any potential security threats and regularly update our security protocols to stay ahead of new vulnerabilities. These features collectively contribute to making Storytell an enterprise-grade, secure platform for managing and interacting with your data. Read our privacy policy, terms of service and data processing agreement for more.Storytell Architecture
Building in public with transparency and trust
One way we endeavor to make AI safe and reliable is by building in public as much as we can. We are happy to do a deep dive with your enterprise platform team to share our architecture and evaluate how to best apply it to your company’s needs.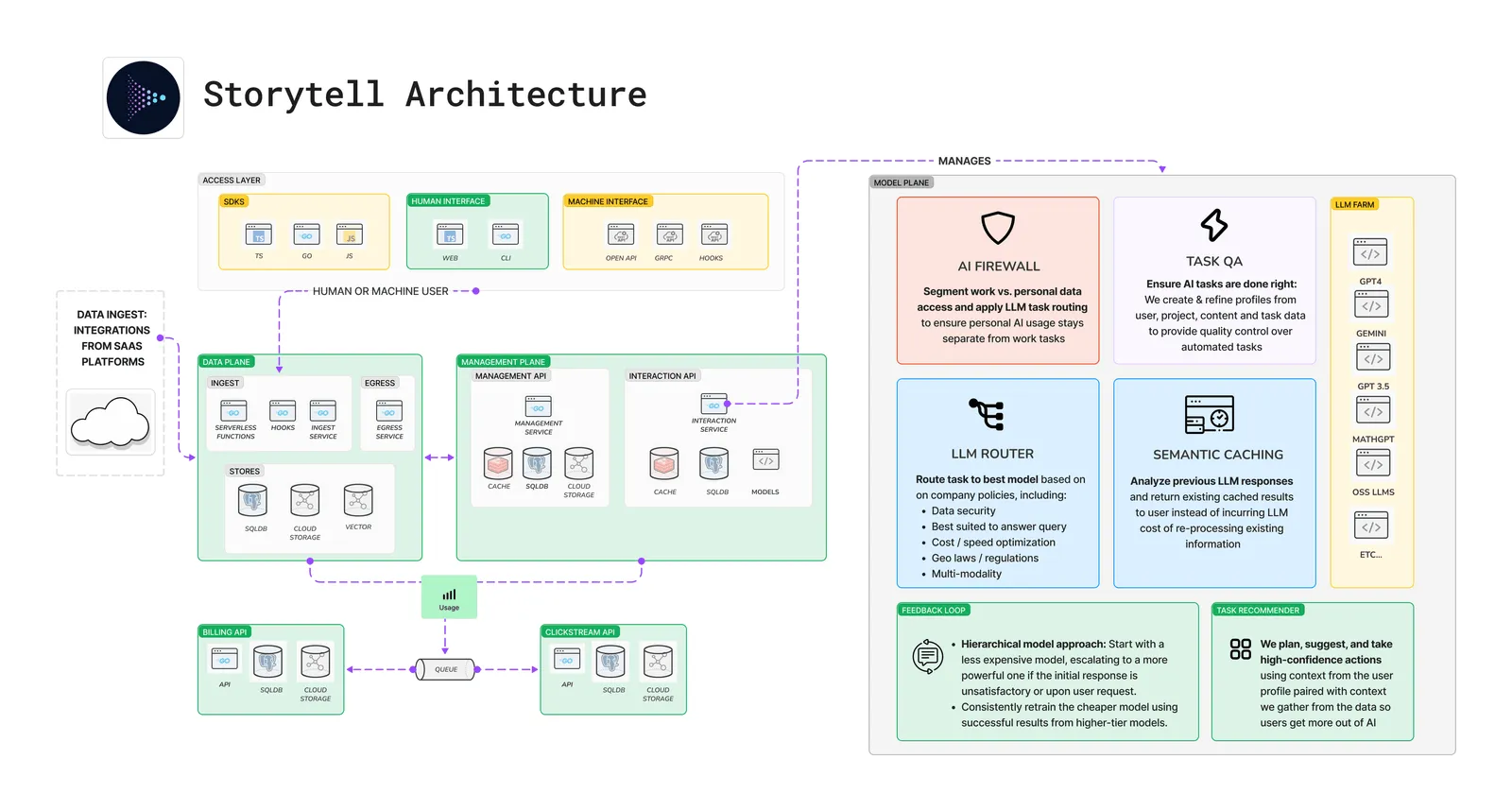 Contact us to schedule a call.
Contact us to schedule a call.